Secure Remote Access and Data Logging for Legacy PLC Systems

Secure remote access and data logging for legacy PLC systems is a practical technical challenge: connecting legacy devices with serial ports and PLCs to modern telemetry, while keeping the operation secure and maintainable. In this HOW-TO, we outline a pragmatic, step-by-step framework that combines hardware and software for deterministic data logging, event handling, and secure remote access.
Secure Remote Access and Data Logging for Legacy PLC Systems: why it Matters
Manufacturers and system integrators face increasing pressure to remotely monitor machines, reduce travel time, and resolve malfunctions faster without exposing critical control networks. By integrating Modbus and Siemens S7 data via OPC-UA gateways or MQTT pipelines, teams gain insight into events, alarms, and performance patterns. At Remote Engineer, we adopt a no-nonsense, engineering-first approach—Machines and us. We understand each other. And you!—to deliver solutions that are secure, controllable, and operationally effective.
How Secure Remote Access and Data Logging for Legacy PLC Systems Works
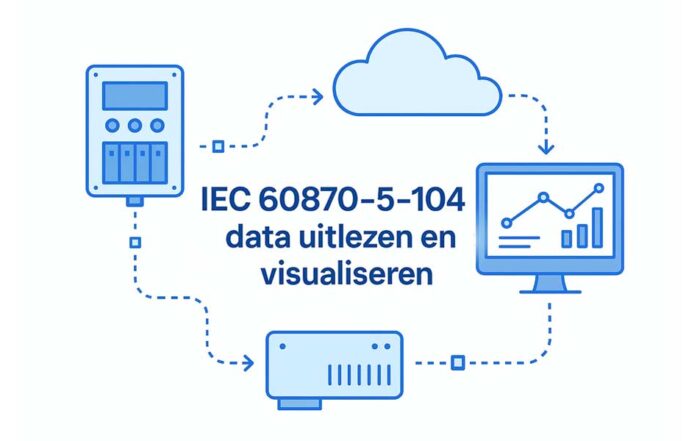
Our typical architecture combines a secure remote-access appliance with local data logging and protocol adapters. Key technical details include:
- Serial Port Bridging: Adapt RS232/RS485 or legacy serial protocols using gateway hardware to make PLC registers available.
- Protocol Translation: Convert legacy serial or proprietary PLC registers to Modbus TCP, OPC-UA, or MQTT topics for modern SCADA and cloud analytics.
- Event-Driven Data Logging: Capture events and status changes (alarms, counters) with timestamps and local buffering to prevent data loss during outages.
- Secure Access: Maintain authenticated remote sessions with end-to-end encryption and role-based access control, keeping IT/OT zones separate.
Step-by-Step HOW-TO Implementation Framework
The following structured steps are intended for technical teams working with legacy equipment such as Siemens S7 and older PLCs:
- Inventory & Risk Scan: Map all PLCs, serial endpoints, and communication interfaces. Consider legacy limitations (baud rates, parity) and which devices require read-only or write access.
- Choose the Gateway: Select an internal or certified gateway that supports Modbus, OPC-UA, and MQTT. Ensure it can unlock serial devices and translate Siemens S7 data blocks where necessary.
- Local Data Logging Policy: Define which events and registers are logged (alarms, counters, temperatures). Configure local ring buffers with time-synchronized timestamps and automatic export rules.
- Protocol Mapping: Map legacy registers to Modbus addresses or OPC-UA nodes. For cloud telemetry, design MQTT topics with clear hierarchical naming and a QoS that meets your reliability needs.
- Security Hardening: Apply network segmentation, TLS for MQTT/OPC-UA, certificate-based authentication, and firewall rules. Restrict write access for external engineers, log all sessions.
- Test & Validate: Simulate loss of connectivity, high event volumes, and reconnection to verify data logging buffering and event replay.
- Implement & Train: Execute the implementation in phases, document serial port settings, register maps, and emergency rollback procedures. Train service personnel in remote workflows and event review.
Technical Details: Practical Notes for Siemens S7 and Modbus
When working with Siemens S7 devices, use protocol-aware connectors that can correctly interpret DB blocks and cyclic data. For Modbus integration with legacy serial port devices, you must be explicit about endianness and word order. OPC-UA is ideal for structured node models and discovery, while MQTT excels in lightweight event publication and cloud-driven analytics. Always version your mappings and retain original register dumps for audits.
Operational Considerations and E-E-A-T in Practice
Remote Engineer’s approach is rooted in practical experience: since our first remote access project in 2008, we have developed proprietary hardware and software to address precisely these challenges. We believe there’s no such thing as ‘cannot be done’—complex problems require careful delineation and practical engineering. Our team of specialists focuses on authoritative, repeatable methods: a clear inventory, tested protocol mappings, and measurable KPIs (reduction in machine downtime, mean time to repair).
Trust is built through transparency: maintain change logs for data logging rules, explicitly track event retention policies, and securely store recordings of remote sessions where policy permits. These practices support audits and continuous improvement.
Checklist: Minimum Viable Implementation
- Device inventory with serial port settings and PLC types (including Siemens S7)
- Gateway that supports Modbus, OPC-UA, MQTT
- Local data logging buffer with event replay
- Encrypted remote access with RBAC and session logging
- Test plan for network loss and high event volumes
Next Steps and Contacting Remote Engineer
If you want a proven HOW-TO tailored to your situation—whether it involves legacy PLCs, serial sensors, or multi-protocol locations—Remote Engineer can define a pilot that demonstrates secure remote access and reliable data logging with measurable value. We combine proprietary hardware and software to deliver solutions quickly and pragmatically. Read more or contact us via www.remoteengineer.eu.
By following this framework, you reduce service trips, improve event response times, and create a secure data foundation for analytics and predictive maintenance, while preserving investments in legacy systems.